Infrastructure
The following is a somewhat complete overview of the infrastructure running on this machine. I regret using Mermaid - manually drawing the setup using Drawio would've been smoother
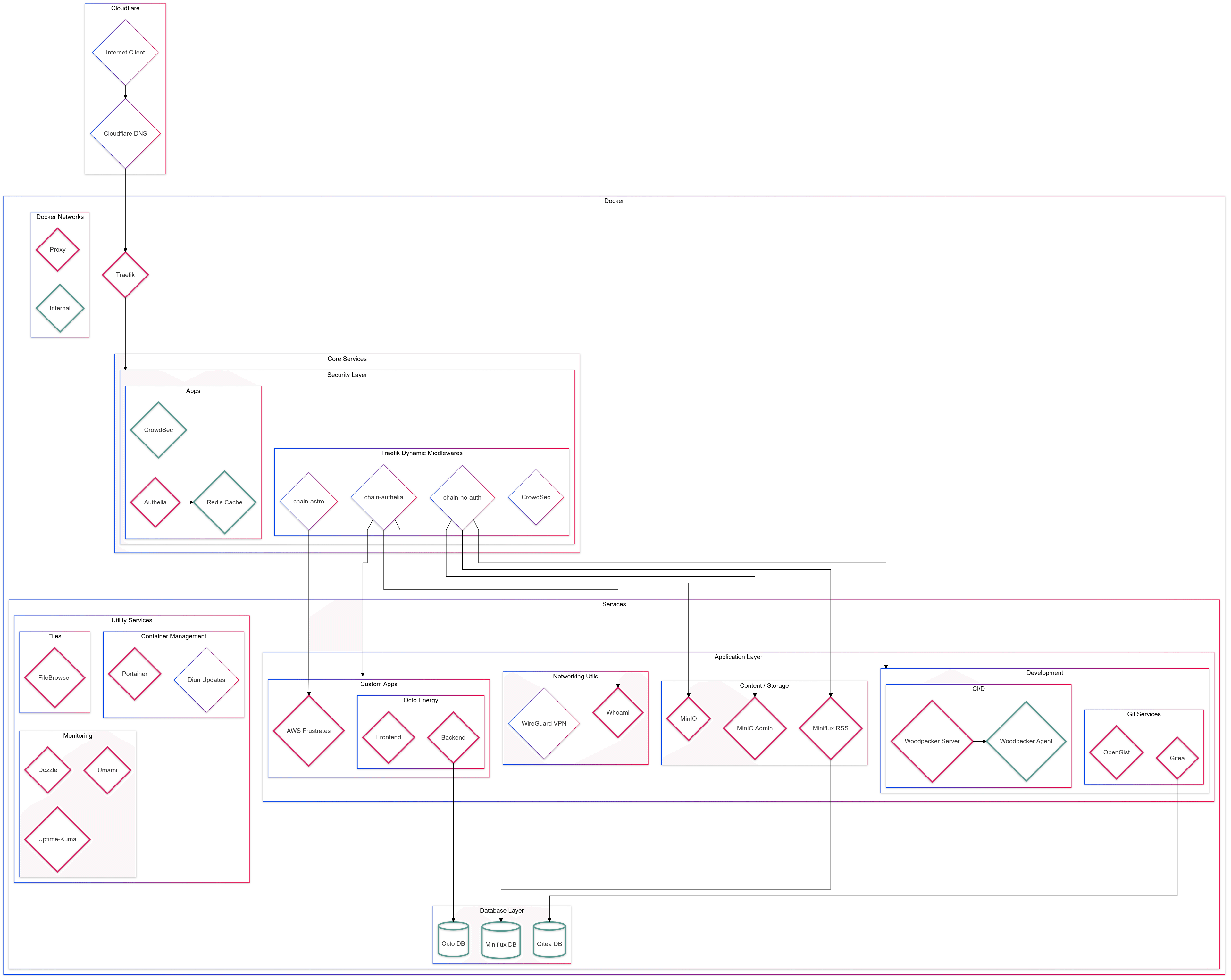
Core Infrastructure Components
Traefik (Reverse Proxy)
Traefik is configured with several key features:
- Automatic SSL certificate management through Cloudflare DNS
- HTTP to HTTPS redirection
- Integration with Crowdsec for security
- Dashboard access through Traefik Dashboard
- Two-factor authentication requirement for the dashboard
Authelia (Authentication)
Authelia serves as the authentication middleware, providing:
- Multi-factor authentication capabilities
- Integration with Redis for session management
- Granular access control through policy configuration:
- Public access to specific domains (e.g. This website)
- One-factor auth for services like Whoami
- Two-factor auth for admin services like Traefik dashboard
- Bypass rules for specific API endpoints and services
Security Layer
The stack includes several security-focused components:
Crowdsec
- Acts as an automated threat detection and response system
- Monitors logs from various services
- Integrates with Traefik through a bouncer plugin
Development and Operations Tools
Version Control and CI/CD
Gitea
- Self-hosted Git service
- PostgreSQL backend for data storage
- Email notification capability through SMTP
- Protected by Crowdsec bouncer
Woodpecker CI
- CI/CD platform integrated with Gitea
- Consists of server and agent components
- Agent has access to Docker socket for running builds
- Protected by authentication middleware
Monitoring and Management
Portainer
- Container management interface
- Direct access to Docker socket
- Protected by Crowdsec bouncer
Uptime Kuma
- Service uptime monitoring
- Custom dashboard for status overview
- Protected by Crowdsec bouncer
Dozzle
- Real-time log viewer for containers
- Access to Docker logs
- Protected by authentication
Storage and File Management
MinIO
- S3-compatible object storage
- Separate endpoints for admin and regular access
- Admin interface accessible via web-browser
- Regular service protected by Authelia
Filebrowser
- Web-based file management
- Access to host filesystem
- Protected by Crowdsec bouncer
Application Stack
Octopus Energy Monitor
The stack includes a custom application for energy monitoring:
-
Frontend container (
octo-frontend)- Protected by Authelia
- Communicates with backend API
-
Backend container (
octo-backend)- Spring Boot application
- PostgreSQL database
- Protected by Authelia
Securing this app’s backend is done via verifying the request’s user with Authelia and confirming the necessary group is present. Swagger UI is also enabled for the Spring Boot application, the UI is protected by a path matching rule within Authelia to block unregistered users accessing it.
Networking
The infrastructure uses two main networks:
proxynetwork for external-facing servicesinternalnetwork for inter-service communication
This separation provides an additional layer of security by isolating internal services from external access.
Additional Services
RSS Feed Management
- Miniflux for RSS feed aggregation
- PostgreSQL backend
- Protected by authentication
VPN Access
- WireGuard implementation through wg-easy
- UI for managing VPN connections
Update Management
- Diun container for monitoring image updates
- Pushover notifications for update alerts
- Direct access to Docker socket for monitoring
Security Implementation
The security model follows a defense-in-depth approach:
-
Edge Security
- Traefik handles SSL termination
- Automatic HTTPS redirection
- Cloudflare integration for DNS and proxy
-
Authentication Layer
- Authelia provides flexible authentication policies
- Redis backend for session management
- Multiple authentication factors available
-
Threat Detection
- Crowdsec monitors for security threats
- Integration with multiple services
- Automated response through bouncers
-
Network Isolation
- Separate networks for different security contexts
- Internal services isolated from external access
- Controlled exposure through Traefik
Disclaimer:
- The diagram is incomplete and probably mis-aligned in places
- This isn’t a full deep-dive explanation into everything, more of an overarching outline